Digital signature forgery
In a cryptographic digital signature or MAC system, digital signature forgery is the ability to create a pair consisting of a message 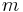 and a signature (or MAC)
and a signature (or MAC) 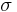 that is valid for
that is valid for 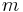 , where
, where 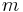 has not been signed in the past by the legitimate signer. There are three types of forgery: existential, selective, and universal.[1]
has not been signed in the past by the legitimate signer. There are three types of forgery: existential, selective, and universal.[1]
Contents |
Types[2]:170
Existential forgery
Existential forgery is the creation (by an adversary) of at least one message/signature pair 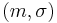 , where
, where 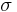 was not produced by the legitimate signer. The adversary need not have any control over
was not produced by the legitimate signer. The adversary need not have any control over 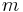 ;
; 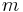 need not have any particular meaning; and indeed it may even be gibberish — as long as the pair
need not have any particular meaning; and indeed it may even be gibberish — as long as the pair 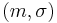 is valid, the adversary has succeeded in constructing an existential forgery.
is valid, the adversary has succeeded in constructing an existential forgery.
Existential forgery is essentially the weakest adversarial goal, therefore the strongest schemes are those that are "existentially unforgeable".
Selective forgery
Selective forgery is the creation (by an adversary) of a message/signature pair 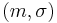 where
where 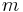 has been chosen by the adversary prior to the attack.
has been chosen by the adversary prior to the attack. 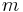 may be chosen to have interesting mathematical properties with respect to the signature algorithm; however, in selective forgery,
may be chosen to have interesting mathematical properties with respect to the signature algorithm; however, in selective forgery, 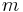 must be fixed before the start of the attack.
must be fixed before the start of the attack.
The ability to successfully conduct a selective forgery attack implies the ability to successfully conduct an existential forgery attack.
Universal forgery
Universal forgery is the creation (by an adversary) of a valid signature 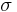 for any given message
for any given message 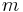 . An adversary capable of universal forgery is able to sign messages he chose himself (as in selective forgery), messages chosen at random, or even specific messages provided by an opponent.
. An adversary capable of universal forgery is able to sign messages he chose himself (as in selective forgery), messages chosen at random, or even specific messages provided by an opponent.
References
- ^ Vaudenay, Serge (September 16, 2005). A Classical Introduction to Cryptography: Applications for Communications Security (1st ed.). Springer. p. 254. ISBN 978-0387254647.
- ^ Goldwasser, S. and Bellare, M. "Lecture Notes on Cryptography". Summer course on cryptography, MIT, 1996-2001